Cisco CCNA 2 Simulation v6.0 Test Chapter 7
-
Questions and answers
Resumen
Cisco CCNA 2 Simulation v6.0 Test Chapter 7 Questions and Answers
CCNA 2 Chapter 7 Quiz Questions and Answers. In this simulation, take your test, get your score and share with others!
- Points: 100
- Questions: 25
- Time limit: None
- Allowed attempts: Unlimited
Exam Chapter 7 Questions and Answers CCNA 2 V6.0
Refer to the exhibit. A router has an existing ACL that permits all traffic from the 172.16.0.0 network. The administrator attempts to add a new ACE to the ACL that denies packets from host 172.16.0.1 and receives the error message that is shown in the exhibit. What action can the administrator take to block packets from host 172.16.0.1 while still permitting all other traffic from the 172.16.0.0 network?

Because the new deny ACE is a host address that falls within the existing 172.16.0.0 network that is permitted, the router rejects the command and displays an error message. For the new deny ACE to take effect, it must be manually configured by the administrator with a sequence number that is less than 10.
Which three statements describe ACL processing of packets? (Choose three.)
Por favor, selecciona 3 respuestas correctas
When a packet comes into a router that has an ACL configured on the interface, the router compares the condition of each ACE to determine if the defined criteria has been met. If met, the router takes the action defined in the ACE (allows the packet through or discards it). If the defined criteria has not been met, the router proceeds to the next ACE. An implicit deny any statement is at the end of every standard ACL.
Which type of router connection can be secured by the access-class command?
Access to vty lines can be filtered with an ACL and applied using the access-class in command.
Refer to the exhibit.
An ACL was configured on R1 with the intention of denying traffic from subnet 172.16.4.0/24 into subnet 172.16.3.0/24. All other traffic into subnet 172.16.3.0/24 should be permitted. This standard ACL was then applied outbound on interface Fa0/0. Which conclusion can be drawn from this configuration?
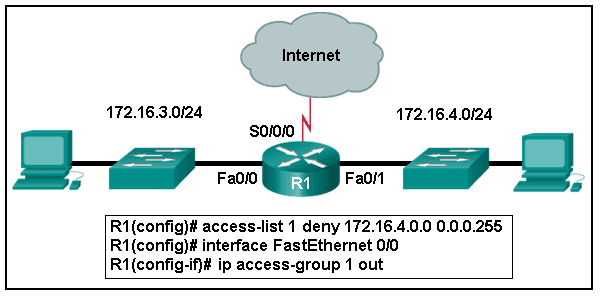
Because of the implicit deny at the end of all ACLs, the access-list 1 permit any command must be included to ensure that only traffic from the 172.16.4.0/24 subnet is blocked and that all other traffic is allowed.
If a router has two interfaces and is routing both IPv4 and IPv6 traffic, how many ACLs could be created and applied to it?
In calculating how many ACLs can be configured, use the rule of “three Ps”: one ACL per protocol, per direction, per interface. In this case, 2 interfaces x 2 protocols x 2 directions yields 8 possible ACLs.
Which statement describes a difference between the operation of inbound and outbound ACLs?
Refer to the exhibit. Which command would be used in a standard ACL to allow only devices on the network attached to R2 G0/0 interface to access the networks attached to R1?

Standard access lists only filter on the source IP address. In the design, the packets would be coming from the 192.168.10.96/27 network (the R2 G0/0 network). The correct ACL is access-list 1 permit 192.168.10.96 0.0.0.31.
A network administrator needs to configure a standard ACL so that only the workstation of the administrator with the IP address 192.168.15.23 can access the virtual terminal of the main router. Which two configuration commands can achieve the task? (Choose two.)
Por favor, selecciona 2 respuestas correctas
To permit or deny one specific IP address, either the wildcard mask 0.0.0.0 (used after the IP address) or the wildcard mask keyword host (used before the IP address) can be used.
Refer to the exhibit.
If the network administrator created a standard ACL that allows only devices that connect to the R2 G0/0 network access to the devices on the R1 G0/1 interface, how should the ACL be applied?

Because standard access lists only filter on the source IP address, they are commonly placed closest to the destination network. In this example, the source packets will be coming from the R2 G0/0 network. The destination is the R1 G0/1 network. The proper ACL placement is outbound on the R1 G0/1 interface.
Which three statements are generally considered to be best practices in the placement of ACLs? (Choose three.)
Por favor, selecciona 3 respuestas correctas
Extended ACLs should be placed as close as possible to the source IP address, so that traffic that needs to be filtered does not cross the network and use network resources. Because standard ACLs do not specify a destination address, they should be placed as close to the destination as possible. Placing a standard ACL close to the source may have the effect of filtering all traffic, and limiting services to other hosts. Filtering unwanted traffic before it enters low-bandwidth links preserves bandwidth and supports network functionality. Decisions on placing ACLs inbound or outbound are dependent on the requirements to be met.
Which address is required in the command syntax of a standard ACL?
The only filter that can be applied with a standard ACL is the source IP address. An extended ACL can use multiple criteria to filter traffic, such as source IP address, destination IP address, type of traffic, and type of message.
What single access list statement matches all of the following networks?
192.168.16.0
192.168.17.0
192.168.18.0
192.168.19.0
The ACL statement access-list 10 permit 192.168.16.0 0.0.3.255 will match all four network prefixes. All four prefixes have the same 22 high order bits. These 22 high order bits are matched by the network prefix and wildcard mask of 192.168.16.0 0.0.3.255.
Which type of ACL statements are commonly reordered by the Cisco IOS as the first ACEs?
ACEs are commonly reordered from the way they were entered by the network administrator. The ACEs that have host criteria such as in the statement permit host 192.168.10.5, are reordered as the first statements because they are the most specific (have the most number of bits that must match).
When would a network administrator use the clear access-list counters command?
The clear access-list counters command is used to reset all numbers relating to ACE match conditions that have been made within a particular ACE. The command is useful when troubleshooting an ACL that has recently been deployed.
What is the quickest way to remove a single ACE from a named ACL?
Named ACL ACEs can be removed using the no command followed by the sequence number.
In which configuration would an outbound ACL placement be preferred over an inbound ACL placement?
An outbound ACL should be utilized when the same ACL filtering rules will be applied to packets coming from more than one inbound interface before exiting a single outbound interface. The outbound ACL will be applied on the single outbound interface.
An administrator has configured an access list on R1 to allow SSH administrative access from host 172.16.1.100. Which command correctly applies the ACL?
Administrative access over SSH to the router is through the vty lines. Therefore, the ACL must be applied to those lines in the inbound direction. This is accomplished by entering line configuration mode and issuing the access-class command.
Refer to the exhibit. What will happen to the access list 10 ACEs if the router is rebooted before any other commands are implemented?

After a reboot, access list entries will be renumbered to allow host statements to be listed first and thus more efficiently processed by the Cisco IOS.
Which feature will require the use of a named standard ACL rather than a numbered standard ACL?
Standard ACLs (whether numbered or named) only filter on the source IP address. Having a named ACL makes it easier at times to identify the purpose as well as modify the ACL.
Match each statement with the example subnet and wildcard that it describes. (Not all options are used.)

What is the effect of configuring an ACL with only ACEs that deny traffic?
Because there is a deny any ACE at the end of every standard ACL, the effect of having all deny statements is that all traffic will be denied regardless of the direction in which the ACL is applied.
Refer to the following output. What is the significance of the 4 match(es) statement?
R1#
10 permit 192.168.1.56 0.0.0.7
20 permit 192.168.1.64 0.0.0.63 (4 match(es))
30 deny any (8 match(es))
The show access-lists command shows how many packets have met the criteria for each ACE in terms of a specific number of “matches.”
A network administrator is configuring an ACL to restrict access to certain servers in the data center. The intent is to apply the ACL to the interface connected to the data center LAN. What happens if the ACL is incorrectly applied to an interface in the inbound direction instead of the outbound direction?
Always test an ACL to ensure that it performs as it was designed. Applying an ACL that is applied using the ip access-group in command instead of using the ip access-group out command is not going to work as designed.
On which router should the show access-lists command be executed?
The show access-lists command is only relevant to traffic passing through the router on which the ACL is configured.
Consider the following output for an ACL that has been applied to a router via the access-class in command. What can a network administrator determine from the output that is shown?
R1#
Standard IP access list 2
10 permit 192.168.10.0, wildcard bits 0.0.0.255 (2 matches)
20 deny any (1 match)
The access-class command is used only on VTY ports. VTY ports support Telnet and/or SSH traffic. The match permit ACE is how many attempts were allowed using the VTY ports. The match deny ACE shows that a device from a network other than 192.168.10.0 was not allowed to access the router through the VTY ports.

Comparte tus Resultados:





